SSH Proxy Jump
Updated:
This post is concerned with the basics of SSH authentication, as well as its indirect login via a proxy server.
Step 1: key pair generation
Use the following command to generate a public(silver)/private(black) RSA key pair under the ~/.ssh/id_rsa directory. The .ssh/id_rsa is the private key that you keep in your machine, and the .ssh/id_rsa.pub is the public key that you distribute to other machines/platforms in order to achieve automatic login via key-pair verification.
ssh-keygen -t rsa
Note that git uses a different type of cryptosystem, namely, the Ed25519 system, which can be generated using the following command.
ssh-keygen -t ed25519 -C "youremail@yourdomain"
Compared to RSA, it is considered to be faster, safer and more compact (Ed25519: 8chars, RSA: 544chars) although RSA is more commonly used.
Step 2: distribute key(s)
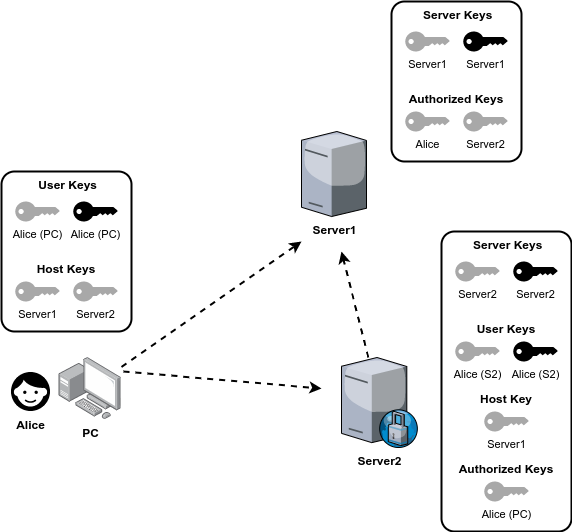
If Alice wants to log in Server1 shown in the figure, she can run the following command to forward her SSH public key(s) to it. The keys sent will be recorded in .ssh/authorized_keys of the host.
ssh-copy-id alice-username@server1.domain-or-ip
Afterwards, Alice should be able to log in Server1 without being asked for her password. I.e.,
ssh alice-username@server1.domain-or-ip
Welcome to XXX ...
Note that for Mac users that do not have ssh-copy-id, you can either intall it via brew or mannually copy these ssh files through scp, rsync or whatnot. If you go for the latter, one thing you should keep in mind is to set the permission bits correctly as shown below.
chmod 700 ~/.ssh
chmod 600 ~/.ssh/*
Step 3: indirect login
In the case that Server1 has a firewall or what have you, Alice has to connect it via a proxy, say Server2; therein lies the question: how to access Server2 directly using key-pair authentication?
To tackle this, Alice can first forward her/his keys to Server2, the proxy, through Step 2. Next, Alice should log in Server2 to generate a key pair (Step 1), and then, send keys to Server1.
Last, but certainly not least, Alice should set up her ssh on her local machine. The configuration (~/.ssh/config) is along the lines of the following.
Host server2
HostName server1-domain
User alice-username
IdentityFile ~/.ssh/id_rsa
Host server1
HostName server1-domain
User alice-username
ForwardX11Trusted yes
ForwardAgent yes
IdentityFile ~/.ssh/id_rsa
ProxyCommand ssh server2 -W %h:%p
Now, everything should be in place. Alice should be able to do login, port forwarding, or whatnot, with automatic key-pair authentication (without having to type her password every single time for every single server along the way!).
🛑 NB: Data loads between Server1 and Server2 is not encrypted.
# Log in *Server1* via *Server2*.
ssh server1
# Tunnelling ports to *Server1* via *Server2*.
ssh -NL {listening_port}:{hostmachine}:{host_port} server1
p.s. Wrestling with company proxies during these COVID times we live in at the moment can be devastating 😷

Leave a comment